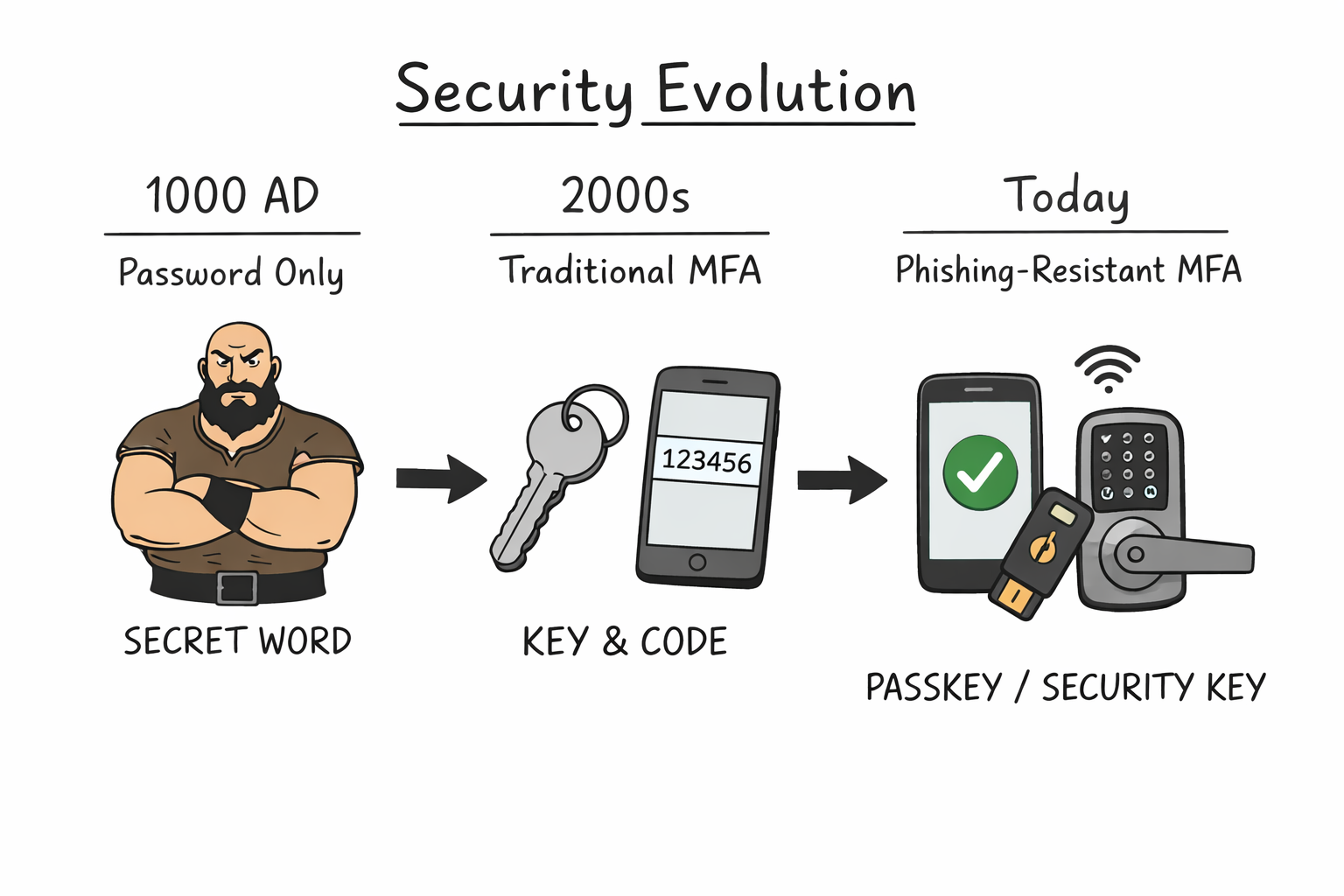
Phishing-Resistant MFA as the modern bouncer — does the analogy hold?

This is part in the series.
Yes, mostly — and it’s a strong way to explain the shift.
Username & password = the old bouncer
A bouncer who:
- Knows your face (username)
- Lets you in if you whisper the right word (password)
The problem:
- Anyone who learns the word can get in
- You can be tricked into revealing it
- The bouncer can’t tell you from an impersonator
That maps perfectly to phishing. Passwords are knowledge-based and therefore stealable.
Modern smart lock = passkeys (device-bound)
A smart lock:
- Doesn’t care what you say
- Only unlocks if you can use the right key (your phone)
The private key never leaves the device (authenticator).
This is a passkey:
- Cryptographic
- Bound to device + service
- Nothing reusable to phish
- Even if someone tricks you, there’s nothing you can hand over
Hardware key — is the comparison fair?
A hardware security key is like a physical high-security key with:
- Unique cut
- Not copyable at a hardware store
- Only works in your lock
Yes: physical locks can be picked, and physical keys can be stolen.
But: it requires physical presence. It also requires skill and effort — and doesn’t scale remotely.
That’s the critical difference.
Phishing scales. Lock-picking doesn’t.
Attacking FIDO2 means targeting the user, not sending 10,000 emails.
Important nuance
Passwords fail at internet scale.
PRMFA (phishing-resistant MFA) forces attacks back to physical scale.
That’s the real win.
Would you protect your home today with:
- A guy who listens to a secret word
- Or a modern lock that only opens for your key?
We upgraded homes.
We upgraded cars.
We upgraded payment systems.
But we still protect company identities like it’s still the year 1000.
Traditional MFA was an upgrade — like adding a physical key.
But we didn’t stop there for our homes… so why did we stop for our work identities?
Passkeys are becoming a hot topic, but few organizations are adopting them at scale.
Yes, Conditional Access and good endpoint security matter — but PRMFA is the shift that removes the phishable secret and breaks phishing at internet scale.
So — does the bouncer analogy hold in your organization? What’s blocking passkeys: apps, devices, or just change management?
Comments
Leave a Comment
Reply to Comment
No comments yet. Be the first to share your thoughts!