Defender for Identity now scans AD for exposed passwords in Comments

If you’ve worked with on-prem Active Directory for a while, you’ve probably seen passwords stored in user attributes and notes, especially for service accounts and shared accounts.
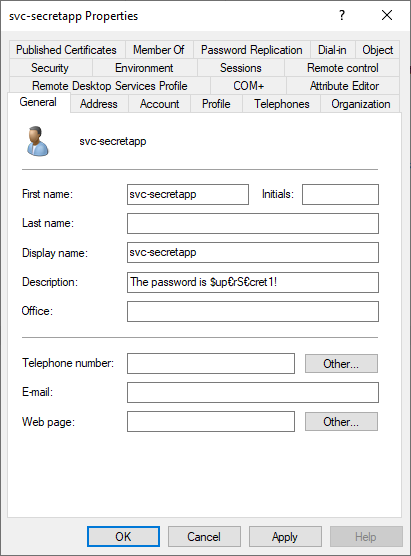
Microsoft Defender for Identity now adds a much-needed feature that scans common AD attributes — including the comments/description fields — for passwords and other credential artifacts, helping you find and remove secrets hiding in plain sight.
See Microsoft’s guidance for details: https://learn.microsoft.com/en-us/defender-for-identity/remove-discoverable-passwords-active-directory-account-attributes
Why this matters
Historically, admins and service owners have used AD attributes like description, info/notes, or custom fields to stash hints, break-glass details, or quick fixes. Defender for Identity’s new detection reduced this risk by programmatically identifying where credentials or credential-like strings are stored in account attributes, so you can remediate it before an attacker discovers them.
The benefits
- Faster exposure reduction: Automated discovery highlights risky attributes for users and service accounts, accelerating cleanup without manual audits.
- Better incident prevention: Removing credentials from searchable directory fields eliminates a common lateral movement and privilege escalation path used by threat actors after initial access.
- Continuous governance: Ongoing monitoring, instead of one-time analysis efforts, gives you a continuous control, which aligning with least-privilege and secret-management best practices.
What happens if you don’t manage this
- Silent privilege escalation: An attacker who gains a foothold can query AD, harvest passwords from attributes, and move laterally—often straight into service accounts with elevated rights.
- Hard-to-trace breaches: When passwords are “hidden” in comments, compromise looks like normal AD reads. Detection comes late, impact is high.
- Compliance and audit findings: Storing secrets in directory attributes violates most security baselines and can trigger audit issues or regulatory nonconformities.
- Operational fragility: Rotations and staff changes break “comment-based secrets,” leading to outages—or worse, leaving stale but still valid credentials behind.
What to do next
Enable and review Defender for Identity’s exposed credential findings, prioritize high-privilege and service accounts, remove any secrets from AD attributes, and migrate to a proper secret store/password manager with documented processes. Pair this with password rotation, just-in-time access, and routine AD hygiene checks to keep the directory clean going forward.
'Til next time...
Comments
Leave a Comment
Reply to Comment
No comments yet. Be the first to share your thoughts!